
How to Crack WEP / WPA Step by Step
KisMAC for Dummies & Step by Step KisMAC Tutorial
KisMAC Tutorials for dummies, beginners & advanced users
Update of update : a Brand New Improved Video in HD, con la musica muy entertaining is available.
Before you post a question, PLEASE be sure to Read the 3 following post:
KisMAC + KisMAC troubleshooting + KisMAC Q & A
If you are looking for the Best Wifi card to be used with KisMAC, the Benchmarks and Tests are HERE
Once you are sure that the answer to your question can not be found, Please, Post your question in the Q&A Article: CLICK HERE.
Cracking WEP with Re Injection
Cracking WEP without Re Injection (Airport, Airport Extreme)
Cracking WPA
KisMAC Troubleshooting Guide
KisMAC Resources Dictionary file, Password list, etc
KisMAC is a free WIFI Network discovery tool and has a large array of powerful features: Detection, Authentication, Injection, GPS, and the ability to crack WPA & WEP keys.
KisMac is really powerful and leave Windows based NetStumbler in the dust. By a large margin.
Kismac is not for absolute beginners and the first step with KisMAC is to read the FAQ. The second step is to read the FAQ again.
Just a little legal warning:
- It is illegal to download, possess, and/or use Kismac in Germany, Austria, Switzerland and Lichtenstein (StGB § 202c)*
- It is illegal, in most countries, including the USA, to crack or attempt to crack, penetrate, listen to, intercept, or “Inject” any WI-FI network others than yours, or Networks where the unequivocal permission was not given to you by the rightful owner.
- Kismac is a tool that should be used on the sole purpose to check and/or verify, audit your own network
Now that I warned you :-) you can enjoy it!
Cracking WEP with Re-Injection
Whatever you do, if you have an injection device (WIFI card or USB Adapter) DO NOT install the drivers of the card / USB adapter.
DO NOT INSTALL DRIVERS FROM THE CD PROVIDED WITH THE DEVICE
How to Crack WEP Step by Step
This tutorial is solely for you to audit your own network. I take no responsibility whatsoever, implied or not.
If you NEED an access, just ask politely your neighbor and either share the cost or discuss with him. A six-pack can be used as lubricant.
Cracking with Injection device

(Hawking HWUG1 shown here, RT73 Chipset)
Do not buy any Network Adapter unless you have read the review.
The most successful method by far, with one little issue: you will NEED a Re-injection device: Either a USB WIFI Adapter or a WIFI card.
But, here comes the trick:
-You cannot use any WIFI card: You must use specific ones.
The list of “approved” hardware is here: http://trac.kismac-ng.org/wiki/HardwareList
As of today, you can NOT inject packet with your Airport / Airport Extreme Apple card alone.
Step 1
Download KisMAC from a trusted source such as: http://trac.kismac-ng.org/wiki/Downloads
Install KisMAC
Plug your Injection device, Whatever you do, DO NOT install the drivers of the card / USB adapter, or you may dearly regret it.
Start KisMAC
Step 2
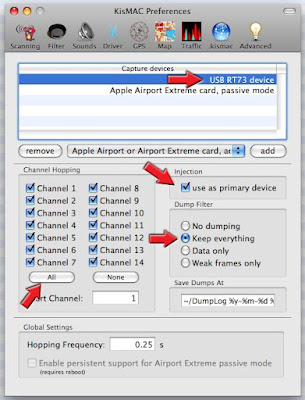
On the Tab KisMAC >>> Preferences >>>Drivers
Select your Injection device i.e. : “USB RT73 device”
If you have a doubt on what to choose, check the "approved" hardware list.
Click on “Add”
Check box “Use as primary device”
Select
Check box “keep everything”
Close Dialog Box
Step 3
On the main screen, select “Start Scan”
KisMAC is now listening to the accessible networks
Look for a network with a WEP key (column “ENC”), a good signal as well as traffic (see Packets and Data)
OR
Enter “WEP” on the search box (top right) and select “encryption” to filter the results
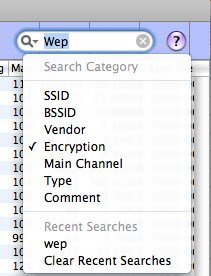
If the Column ENC is “NO”, the network is OPEN: No need of cracking anything
Once you have selected a network, look for the CHANNEL of the network, i.e 1, 2 etc …
Go back to Preferences >>>> Drivers
Select only the Network selected i.e 1
Step 4
Let KisMac work for 5 minutes collecting data
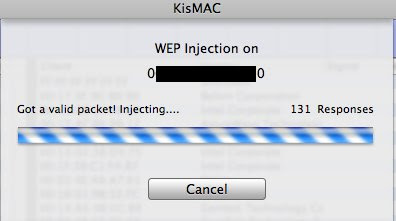
On the “NETWORK” Tab, select “Reinject Packets”
KisMAC will now try to reinject packets to speed up the process
Keep an eye on the “Unique IV’s” number, once it has reach at least 130,000 (200,000 is recommended) you may start considering cracking.
Step 5
Once you have collected enough, On the NETWORK Tab, Select “Crack” >>> “Weak Scheduling Attack” >>> “Against Both”
KisMAC will now try to crack the key…
Reminder: the more Unique IV’s you have collected, the greater are the chances to crack the key.
I have experienced crack as fast as 10 sec with 200,000 Unique IV’s (on a 64 bit key) and sometimes 30 minutes with only 110,000
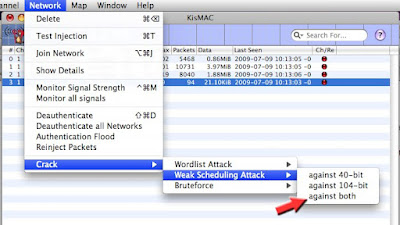
If you know for sure that the key is either 40 bit or 104 bit, then select the appropriate one. If you are not sure, select "both"
40 bit is a 64 bit (40+24)
104 bit is a 128 bit (104+24)
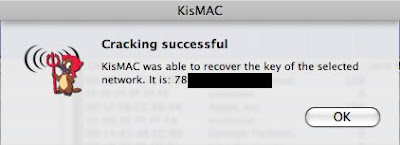
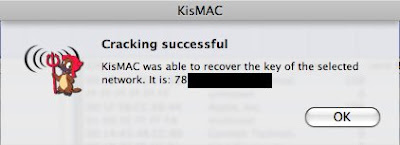
If you have followed the steps, you should see something like that appears :-)))
remove the semicolon, and there you have it, or take a look at the main screen under Key or ASCII Key
How to crack WEP /WPA with Airport Extreme, Passive mode
WITHOUT Injection Device (Airport, Airport Extreme Alone)
WEP attack
Download KisMAC from a trusted source such as: http://trac.kismac-ng.org/wiki/Downloads
Last build is 0.2.99 , build 0.3 is coming soon.
Install KisMAC
Start KisMAC
Step 1 (without an Injection Device)
On the Tab KisMac >>> Preferences >>>Drivers
Select your card. (Capture devices) i.e : Airport Extreme Card, Passive Mode
Click on “Add”
Select “All Channels”
Close Dialog Box, and select “Start Scan” on the main window
A dialog box opens and load the card. Your Admin password may be required.
Step 2
KisMAC is now listening to the networks accessible
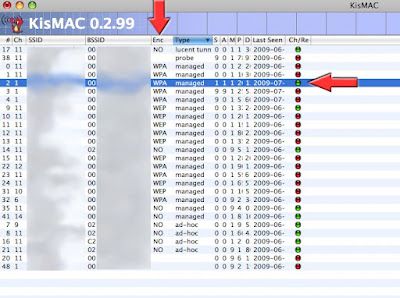
Look for a network with a WEP key (column “ENC”), a good signal as well as traffic (see Packets and Data)
If the Column ENC is “NO”, the network is OPEN: No need of cracking anything
Once you have selected a network, look for the CHANNEL of the network, i.e 1, 2 etc …
Go back to Preferences >>>> Drivers
Select only one Network selected i.e Channel 1
Step 3
Be patient: open a beer, pour yourself a nice glass of wine or have a nice cup of coffee.
Without an injection device, you will need to collect a minimum of 130,000 unique IV’s before you can start cracking a 40/64-bit WEP
Recommended:
200,000 Unique IV’s for weak scheduling attack on a 40/64-bit WEP
1,000,000 Unique IV’s for weak scheduling attack on a 104/128-bit WEP
Or
500,000 packets for weak scheduling attack on a 40/64-bit WEP
2,000,000 packets weak scheduling attack on a 104/128-bit WEP
It may take a long time….
Step 4
Once the packets are collected, Go to the tab “Network” >>> Crack and select the method,
For a start, I would suggest: “Crack” >>>”Weak Scheduling Attack” >>> “Against Both”
Once started, you’ll have to wait between 5 and 20 minutes depending on your machine for KisMAC to try all the keys.
The more packets you have collected, the better are your chances to be able to crack the key.
WPA crack / Attack
>>>>> Packets RE-Injection DOES NOT WORK on WPA attack <<<<<<
>>> I said RE-Injection and not "Injection"
In order to crack a WPA key, you'll need the handshakes, a serious dictionary file or fileS and a LOT of CPU time. Hours and probably days of it. (read the "I am bored part" at the end)
You first need to capture 4-way EAPOL handshakes (connection between the computer and the network) -When captured, you'll see the Ch/Re red dot turns green. You are ready to try...
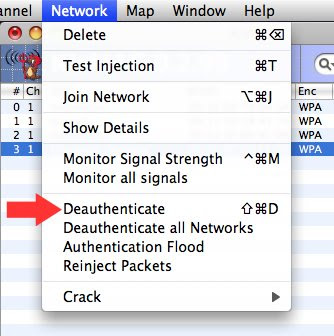
To speed up the process of capturing the 4-way EAPOL handshakes, you can try a deauthenticate attack: it will force the network to shutdown and restart, hence speeding up the process. In order to Deauthenticate, you'll need a USB Network Adapter. Airport alone can not Re-inject (as of 2010)
Go to Network >>> Deauthenticate
Some network may recognize the attack and change channel.
Once the Ch/Re is ready, Go to the tab "Network" >>Crack >>WPA
It will then ask you for the dictionary file, select the file you want to use, and start...
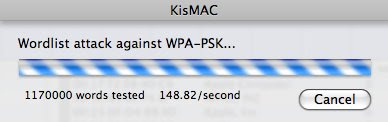
Nota Bene:
KisMAC will try every word (from the list provided) to attempt to crack the key, hence it may take a lot of time....if you have a slow machine, be really patient.
I have a not so bad machine, and I run about 170 words per second. You can leave a comment with your config and speed for me to compare.
Mine: MacBook Pro 2.5GHz Intel Core 2 Duo + 4GB DDR2 SDRAM : about 170 Word/sec
As for the Dictionary files, you can find links on the KisMAC website or take a look at the "RESSOURCES" post.
Note on dictionary files:
Wordlist = dictionary file
- The words are tested "as is" and not in combination.
Example: the password is "I love Kismac"
If your dictionary contains the words "I" + "love" + "Kismac" it will NOT work, your wordlist must contain the exact (verbatim) "I love Kismac" as a word to successfully attempt to crack.
The files must be a text format .txt and contain a empty line at the end.
KisMAC Troubleshooting Guide , KisMAC Issues, KisMAC Ressources are on the NEXT post....
KisMAC for Windows, ditto...next post
WPA: Wordlist links and files uploaded here
Like this Article? SHARE IT!!!
☟ Use the Share Button ☟
Don't like this Article? Share It With People You Don't Like!!!
Don't like this Article? Share It With People You Don't Like!!!
Know Something worthy of mentioning? Leave a comment and earn brownie points!




has anyone come up with a driver for the ALPA AWUS036NH ?
ReplyDeleteI already have that unit and I hate to buy another one if it will be possible to use it.
Not for KisMAC. See Linux.
ReplyDeleteA little about speed of WPA brooteforse:
ReplyDeleteI have the same configuration: MacBook Pro, 2.3GHz i5, 8Gb DDR3. But i use aircrack to crack WPA handshakes.
It's simple to install aircrack. You'll need mac ports http://www.macports.org/install.php
After install, type in terminal:
#sudo port install aircrack-ng
You can use it!
And the speed of bruteforce is of about 1.6-1.8K passwords/sec.
Ilya,
ReplyDeleteYou don't crack the "Handshakes". The handshakes are the 4 way EAPOL that are needed to compute the Pairwise Master Keys.
Also, the "speed" is not in Passwords per Seconds, but in keys (pairwise master key)
As for 1600 k/s. it is still very slow compared to what you can achieve:
http://easymactips.blogspot.com/2011/07/kraken-has-been-released.html
I did a wordlist attack and found the key for a WPA network.
ReplyDeleteWhen I click on Join Network while that network is selected nothing happens.
I don't know what to do know and unfortunately there's not any information about this stage in Kismac site.
I'm on os x 10.7.5 and using AWUS036H
Mayor,
DeleteDon't use "Join Network" , it does not work. Look at the key and copy it to Airport or Realtek.
could this one work with Kismac? thx
ReplyDeleteUSB Rt3070 Chipset 802.11n 150m Wifi Wireless-n Card Dongle Adapter
http://ebay.to/2jGfQDp