Troubleshooting KisMAC
KisMAC Tutorial
Resources
Troubleshooting KisMAC
KisMAC 0.3 Bugs
KisMAC 0.3 Issues
KisMAC 0.3 Not Working
- KisMAC 0.3 is for Snow Leopard 10.6
Can't Scan with KisMAC 0.3
"NOTE: If a previous installation of KisMAC has been used, please make sure to delete the following files, if they exist:" ( '~' is your home folder) (
Using App Cleaner IS a GOOD IDEA)
- ~/Library/Preferences/de.binaervarianz.kismac.plist
- ~/Library/Preferences/com.kismac-ng.kismac.plist
- ~/Library/Preferences/org.kismac-ng.kismac.plist
Message
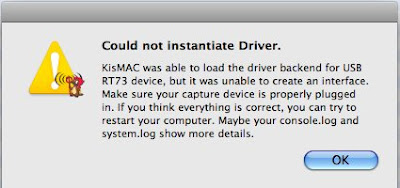
Could not instantiate driver. KisMAC has not been able to load the driver backend
Could not initiate driver. KisMAC has not been able to……
Whatever you do, if you have an injection device (WIFI card or USB Adapter)
DO NOT install the drivers of the card / USB adapter.
Possible causes:
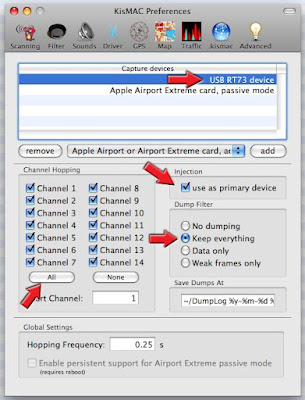
You have NOT selected "Use As Primary device"
You Have NO Drivers selected
You have Selected the Wrong one
Your Chipset is not supported (see Hardware list)
The Chipset of your USB Network Adapter is not correct (See FCC Number)
If you look in your console.log (Spotlight >> Console.app)
you'll probably see a lot of lines with KiMAC as "sender" and an error messages such as:
KisMAC[2928] vendor 1452 vendorId 3574 product 32773 productId 38674
KisMAC[2928] Matching finished
KisMAC[2928] Error could not instantiate driver WaveDriverUSBRalinkRT73
Reading the last line, you can easily guess where the issue comes from: RT73 driver can't be loaded. Why? because you specified to KisMAC not to, or Specified to KisMAC to load the wrong one.
Solutions
Select Appropriate Driver or use the proper USB Network Adapter. You may need to Force Quit the application
You have installed drivers provided with the CD of your USB Network Adapter.
Solution 1:Time machine? if you have Time Machine set up, pat yourself on the shoulder: smart guy!
If not, time to think about it and move onto Solution 1.5
Solution 1.5:
Uninstall the drivers and the all shebang provided with your injection device
including the proper .plist for Kismac
use AppCleaner to remove all .plist
OR if you had a previous install, remove the following, if any:
~/Library/Preferences/de.binaervarianz.kismac.plist (where '~' is your home folder)
~/Library/Preferences/com.kismac-ng.kismac.plist (where '~' is your home folder)
~/Library/Preferences/org.kismac-ng.kismac.plist (where '~' is your home folder)
(told ya' use AppCleaner)
Solution 2: If, after uninstalling the drivers, the problem persist,
-and- you have trouble with your Airport Extreme, you may be in for a shitload.
Uninstall KisMAC, and re-install
Solution 3: >> Apple Store, Genius Bar or Re-install OS X with the archive option.
I have experienced advanced trouble by installing drivers provided with an Edimax. It F**** up the Airport Soft, Archiving and re-install was the only working solution for me.
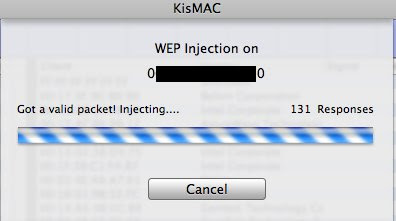
Injection does not work
- Check that your device (USB/Card) is able to inject
- Test injection: Tab “NETWORK” >>>”Test injection”
- Check that you have checked the box “use as primary device” in tab Preference >>> Drivers
- Check that you have the proper driver/chipset selected i.e. USB RT73 or USB RT2570 (Preferences >>>Driver)
- Check that proper channel is selected.
One channel only: You cannot inject while Channel hoping is selected
- As stated, be very careful to have the proper chipset, otherwise: nada!
Word of advice, I would suggest you to test the hardware in a “brick and mortar” shop before you buy something that will not work.
Packet collection is very slow
It’s probably because the network is not very active (low traffic). Just go on YouTube, watch few videos and the packet collection should increase very quickly.
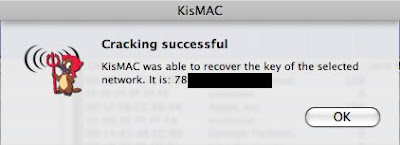
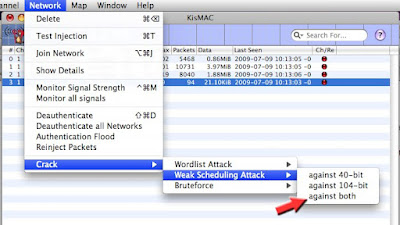
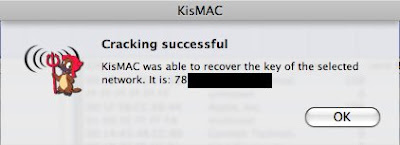
Crack does not work
-Well, as stated in the FAQ, Injection is the bleeding edge of this technology, and I have experienced myself some failures with my own network: I was unable to crack my own key with more than 1,000,000 unique IV’s.
Other possible causes:
The key was changed during the collection
You have selected a 40/64-bit WEP when the key is 104/128-bit WEP, so in doubt, play safe and select both
You have encountered a SOL error: Shit Out of Luck
The wpa key could not be recovered because of the following reason:
the key was none of the tested passwords.."
Most likely, your dictionary file does not contain the exact password, read the article about wordlists.
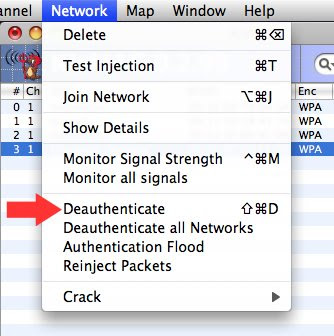
WPA Reinjection Does Not Work
please note that RE-Injection and Injection are not the same.
-WPA RE-injection will
not work, you can only RE-inject on WEP network, if you have an injection device. (i.e When you Deauthenticate , you are injecting frames)
Could not load Airport Driver
KisMAC could not attach to the Apple Airport Driver
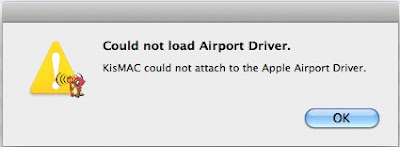
This Error Can Have Multiple Origins, Please Read Carefully.
KisMAC could not attach to the Apple Airport Driver
In Preferences >>> Driver
You may not have selected any Driver (Apple Extreme, RT73, etc etc )and pressed the "Start Scan" button multiple times, this provokes a freeze and return this error.
The "Start Scan" button looks like the one in the picture below (button engaged)
The solution is a Force Quit and to select a correct driver in Preferences >> Driver
KisMAC could not attach to the Apple Airport Driver
Cause: Airport, Airport Extreme in ACTIVE Mode
This issue is fairly new and is related to the brand new Snow Leopard (10.6)
You have this error because you have selected
Active Mode
Close KisMAC , re-open and select
Passive Mode.
Do not use Active Mode with OS X 10.6 until further notice.
No Driver Selected
Please Select a WIFI Driver
Go back to Preferences and Select a Driver
i.e. Airport Extreme Passive Mode, USB RT73 Device, or else.
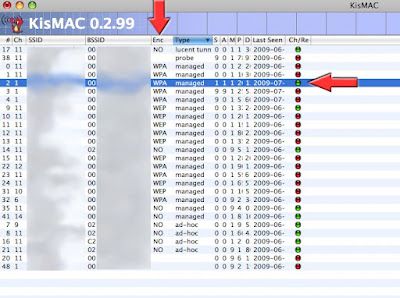
KisMAC Ch/Re Gem
The Ch/Re Gem is situated on the last column, right after "last seen"
Ch/Re stands for Challenge / Response
The Gems have 3 colors possible: Green, Orange and Red and the meaning will depends on the type of encryption of the Channel/Network
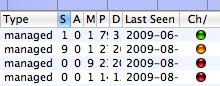 Enc = NO
Enc = NO
The Network has no encryption (Open), (under column "Type") the Ch/Re Gem is green by default
Enc = WEP
The Network is encrypted by a WEP key, the Ch/Re Gem is red by default and indicates that Kismac does not have recovered a key (yet) No Challenge or No Reponse
Green Challenge or Response
Orange has a Challenge OR a Response
Enc = WPA
Red: No handshakes captured, don't even try a wordlist
Orange: Capture Started (?)
Green: Handshake Captured
KisMAC Freezes
KisMAC Hangs
KisMAC Freeze, KisMAC is hanging, KisMAC Freezes, PinWheel KisMAC
If KisMAC Freezes after few seconds, and hangs (Pinwheel) the first cause that comes to my mind is that you are using (listening to) the wrong channels.
If you are in USA, you should not be using Channels 12,13 & 14 (Europe and Japan)
If you are in Europe, You should not be using Channel 14 (Japan Only)
Just uncheck 12,13 & 14, that should resolve the problem.
Possible cause: Channels 12,13 & 14 are close to the microwave range and cordless phones (old ones)
It's possible that you are listening to your coffee or pop corn.
A second cause could be a large number of router using the same channels (often Ch 6), it may also create issues on your own network. In that case, just switch channels and you'll see an improvement in your Network quality
Can't Collect IV's
Can't Collect Packets
Packets Collection is very slow
I have received a lot of questions about this issue. The most
probable cause is a
non active network.
A non active or slow network (low traffic) is what makes the collection very slow.
KisMAC in passive mode is like trying to collect rain water: The more it rains, the more you can collect. That simple! If it does not rain .... or very little ... you got the idea!
After receiving 10 + questions on the subject, here is an example of a near silent network:
As you can see 614,847 management packet (beacon) and only 25,945 Data Packets (the good stuff)
so, 615,902 junk.
This network is simply "on" but not used, hence, as long as there is no valid traffic, you need to be more than extremely patient
Other possible cause: You may be listening to a Probe, or a Router not connected to the internet, or someone that left his router on, but does not use it. Read the post till the end...
Here is what I have tested with active networks, and very active networks. It clearly shows that the collection of IV's is related to the traffic.
The test is with an
Airport Extreme, Passive Mode, NO Re-injection
It took me 5 minutes to reach 130,000 IV on very active network, and 126 min on Active.
For the numerous persons that still believe that Kismac can not crack on Airport Extreme, the following is going to be surprising:
Very Active Network
Time : 0:02:05 2min, 5 sec
Bytes: 83.42 MiB
Packets 58,423
Unique IV in 0:02:05 = 57,016
U IV/Sec = 456.12
Theoretical Time to reach:
130,000 = 285 sec = 4.75 min
200,000 = 438 sec = 7.30 min
300,000 = 658 sec = 11.0 min
Active Network
Time 03:23:50 3hrs 23 min 50 sec
Unique IV's in 03:23:50 = 210,216
U IV/Sec = 17.18
Theoretical Time to reach:
130,000 = 126 min
200,000 = 191 min
300,000 = 285min
1 As Kismac has loaded the Airport Driver, he has control over it. Proof that this is on Airport and not on USB
2 Time
3 Packets
4 Unique IV's Collected with Airport Extreme on Passive Mode.
a Kismac still on Airport
b Time 2min and 5 sec
c Unique IV's Collected with Airport Extreme on Passive Mode. = 57,016 in 2 minutes, roughly 11 min to 300,000
d Bytes = 83.42 MiB for 57,000 IV's
Hence, Kismac does work on Passive Mode, and yes, you can crack on Passive mode without Re-Injection. If you can't, it's probably because of the network quality or simply because you may have selected a wrong parameter.
Test Your Own
One way to be sure is to test your collection speed:
Go to a friend's house , Start KisMAC , and ask your friend to watch multiple Youtube Video on its network. You want to push the router to the max.
You'll be then able to see if the issue is due to slow network or not.
While you're at it, ask your friend to run KisMAC too: You'll be surprised to realize that you can:
A) exchange PCAP dump files and try multiple cracks on multiple networks
B) if using Re-injection, notice that ONE device will make ALL Macbooks able to pick up the responses
Macbook does not detect edimax ew-7318usg
It's NORMAL! Don't panic!!!
Your Macbook can NOT detect your Edimax, because your driver(s) are not installed*.
KisMAC will detect your edimax, under
Preferences >> Driver >> use USB RT73 Device
DO NOT INSTALL the Drivers provided with the install CD of your Edimax
if you do so, or have done so, please refer to Troubleshooting KisMAC.
*To Check your USB Network Adapter, just go to >> About this Mac >> More Info >> USB
Even if not active it should show in the USB section
Kismac weak scheduling attack takes a long time
A Weak Scheduling attack may take some time, but you (yes, YOU) can make much faster:
Don't start cracking unless you have a mini of 130,000 IV's
200,000 is recommended
You may have collected corrupted packets, Sorry: S.O.L , try again
Rule of Thumb: The More IV's Collected, The Faster The Crack Will Be.
How Many packets I need for WPA?
None! For WPA, you need to capture the Handshakes.
Look at the Ch/Re Gem indicator , or read the post related to that question.
How Many unique IV's for WEP?
Number of unique ivs needed kismac?
It is recommended to start at a minimum of 130,000 unique IV's
You can always try under, but it will probably fail or the key recovery may take much longer.
How fast can I successfully crack a WEP or WPA?
How fast can you crack a WEP key?
You just opened a can of worms ...
WEP
The more IV's you have collected, the faster the crack
should be.
I have successfully cracked my own WEP key in less than 3 sec (128 bits key)
I also have, on the same key, spent hours with no success, .... I had up to 2 millions IV's
I suppose some frames were corrupted, but I can't say for sure. I made a Video on YouTube showing a crack in less than 3 seconds.
WPA
It will depend on your password. If you use a dummy password*: between 5 sec and few hours.
If you use a GRC generated password, you better explain to your kids how to do it: they will continue your work long after you'll be dead. Seriously!
If you NEED an internet connection because you just moved, are in a new place, can't afford the monthly overpriced FIOS or UberDuper connection, then you'll need a SA-6p, SA-12PSA or SA-24PO
it's not software anymore, it's hardware, but I was successful in cracking a WPA2 in very, very, little time.
I have heard of BIM attack with Ha100B series, but I never tried it myself.
BTW: Dummy passwords: lists ARE available :-), I URGE you to use very serious password and avoid at any cost guessable passwords.
Hint: 123456, 1234567, password, letmein, mustang, iloveyou, etc etc ...
PCAP Dump
When you check the box "Keep everything" it start saving a file where a bunch of details are kept.
This file is accessible for later review (advanced user only, please) you can use Wireshark to read that file and discover all the little tiny details ;-)
Console Log (from Console.app)
it's the log of what is happening behind the doors when you use your computer.
If you keep console log open, you may find messages such as "Warning, deauthentication Frame received"
It means that somebody is trying to penetrate your network with a Deauthentication attack. (more exactly, trying to force capture the handshakes)
Like this Article? SHARE IT!!!
☟ Use the Share Button ☟
Don't like this Article? Share It With People You Don't Like!!!
Know Something worthy of mentioning? Leave a comment and earn brownie points!
KisMAC Freeze, KisMAC is hanging, KisMAC Freezes, PinWheel KisMAC